Router Security
Does Router Security Really Matter?
Yes! As the prime element of the network, router need to be secured in physical as well as logical means. If left open, that will be a major vulnerability in the network.
Do you know?
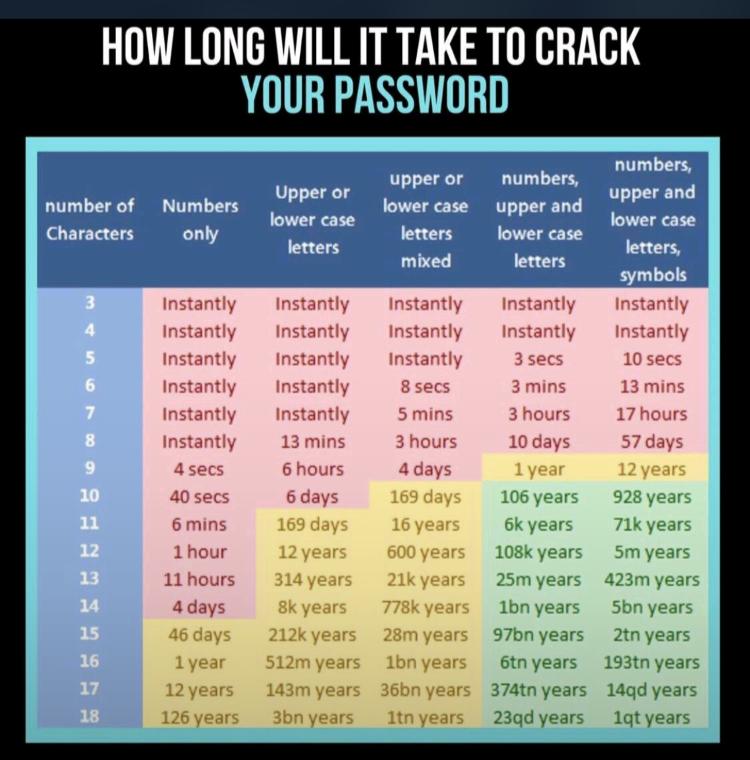
Image 1: Password strength.
How to Logically Secure a Router?
Router can be secured logically by providing password. There are two ways to protect the router with password.
- Clear Text Password
- Password Encryption
Clear Text Password
This is the basic way to secure a router. But not the most effective.
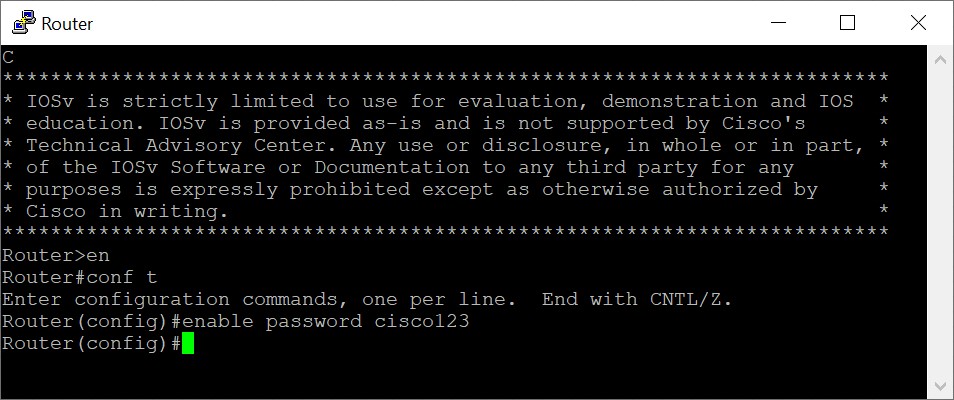
Image 2: Securing a router with clear text password.
For instance, A senior engineer is working on the router console and leaving it open for some time. Meanwhile a network associate can track down the password and could disrupt the entire functioning network if used wrongly. By using the ‘show run’ command, previously done configuration can be seen. Apart from this, the password can also be retrieved from router’s flash memory.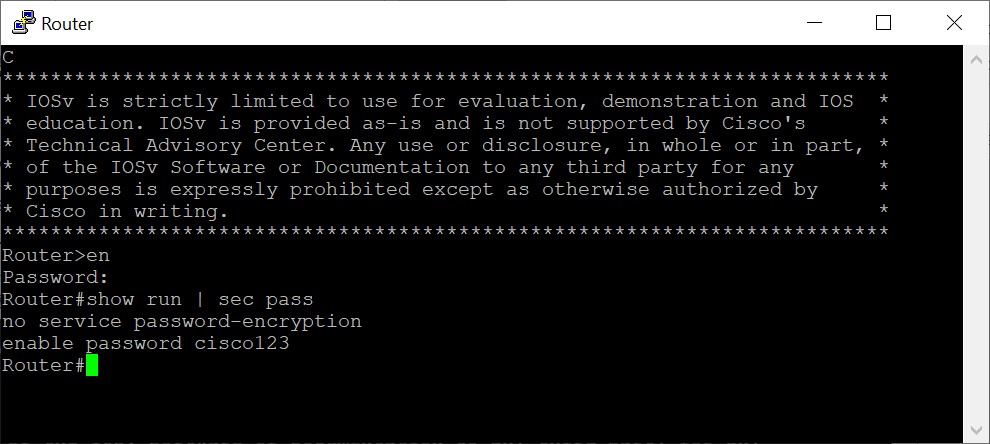
Image 3: Show running-config command shows password in clear text.
Password Encryption
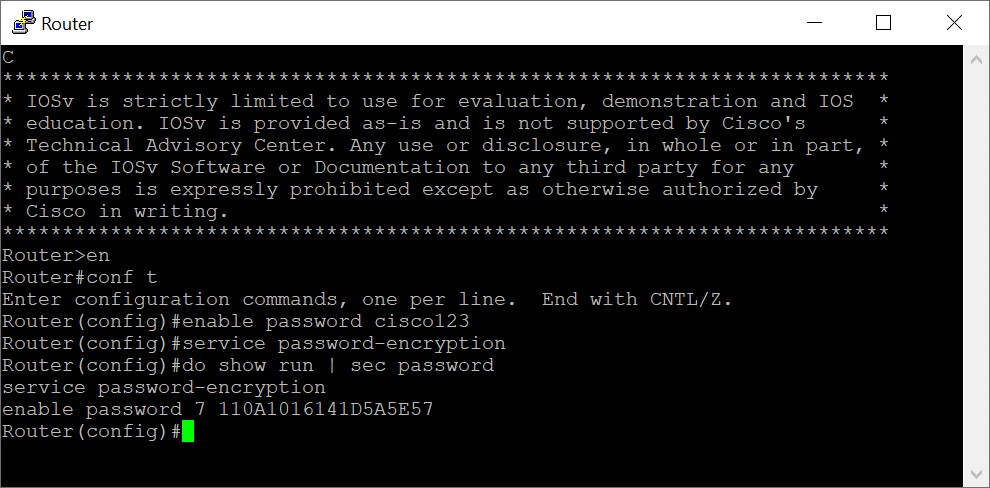
Image 4: Password Encryption.
The command ‘service password-encryption’ is used to encrypt all the passwords in the router. After Encryption, the password is not visible in clear text. But still if a person gets the encrypted password. It can be easily decrypted. There are many password crackers available online.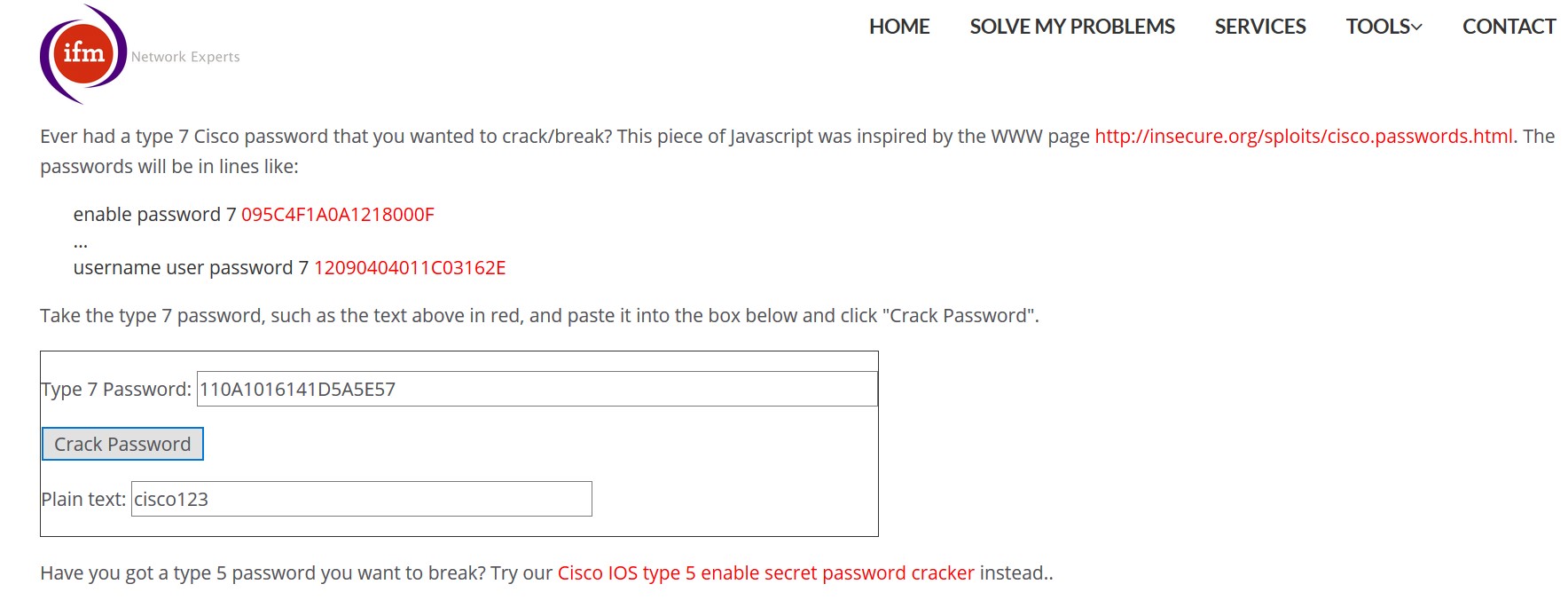
Image 5: Decrypting the encrypted password.
Is there any way to permanently secure a router?
Yes ! In the continously evolving digital era, every problem comes with a solution. In order to secure the password the concept of ‘Hashing’ is introduced. Apart from password encryption, Hashing palys a major role in data integrity.
Hasing is the concept of using algorithm to convert a data of any size to a fixed length hash code. As seen in the above example encrytion is a reversible process. But hashing is a non-reversible process.
Image 6: Hashing.
The following algorithms are used by the Hash generator to convert the confidential data into the hash code.Hash Collision
The event of generation of same hash code for two different data.
Image 7: Algorithms.
Hash Collision has been indentified in MD5 and SHA-1 by IT Giants. But till now there is no such collision identified in SHA-2 and SHA-3.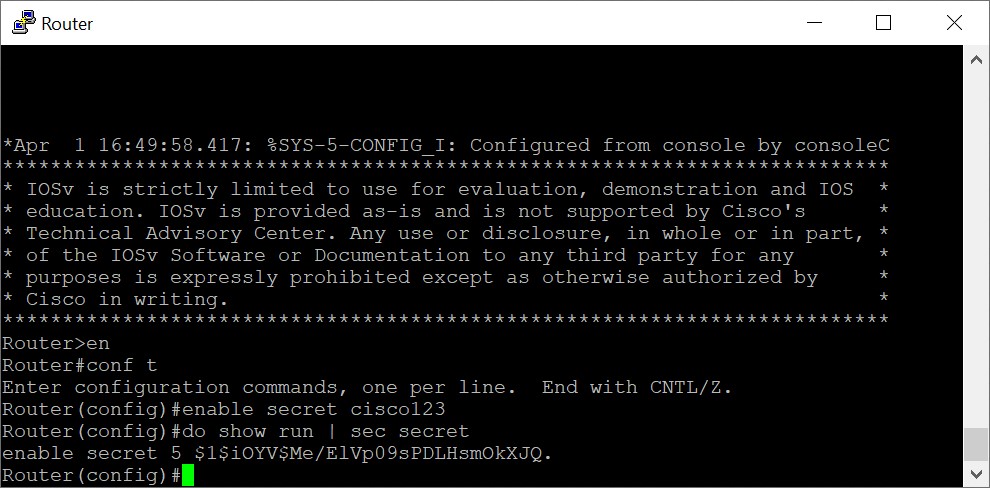
Image 8: Password Hashing.
The Hash code can be retrived from the router but its cannot be decoded as like the encrypted password. As we have seen that hasing is non-reversible but there is a way to find the clear text of the hash code by Brute Force Attack. Brute Force, uses an algorithm to guess the hash code of the password by using combinations.If it is a 1,2 or 3 word password, the algorithm can easily guess the hash code of the password. But if the password is more complex with more than 6 characrers or with special characters then it will take months or years to guess the hash code of the password using combinations. That’s why every internet banking site, social media site and many mandates the usage of complex passwords. Also they are insisting the users to change the password in a timely manner.
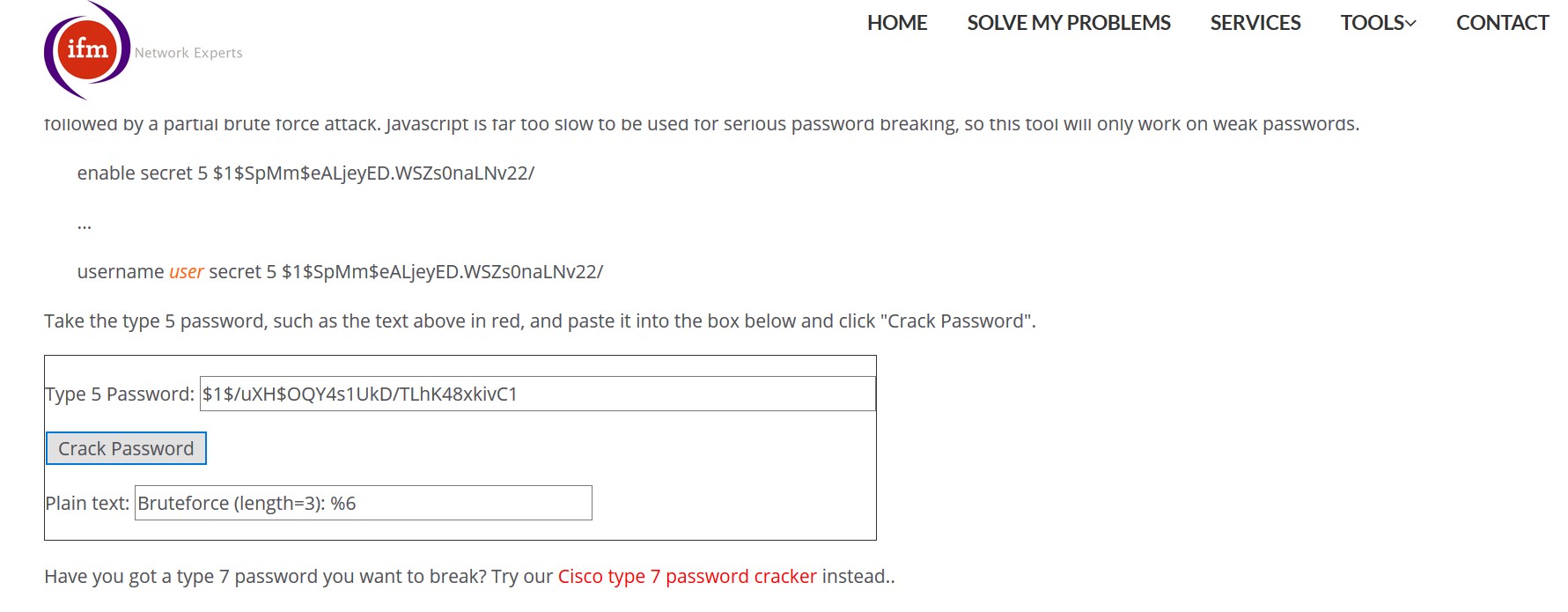
Image 9: Brute Force Attack.
List of CISCO IOS commands used:
- enable password password Used to set password for enable mode
- service password-encryption Used to encrypt all the passwords in the router
- no enable password Used to remove the password
- enable secret password Used to hash secure a password while setting
- no enable secret Used to remove the hash secured password
- show running-config Used to show the running configuration of router
